Provides audit and compliance support, assisting with meeting requirements for government, corporate, and industry regulations.
Supplement, expand or replace existing Security Operations Center (SOC) capabilities and provide training for other SOC analyst and other security engineers.
Provide technical and analytical expertise to support the modernization of cyber development, operations, infrastructure, and training for partner organizations.
Corporate Partners who have incorporated our applied learning initiative have found co-op opportunities to be more cost effective than traditional outsourcing while providing more meaningful benefits and services.

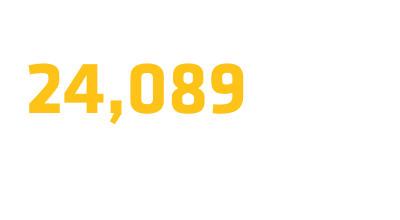


We provide student employees that are high quality, performance focused, better prepared, and eager to work and learn. As a CSFRG Employer Partner, we save you time and money:
In addition, our WSU Career Coaches work with students to ensure they are equipped to be successful in their professional roles. They also serve as advisors and liaisons--ensuring your needs are met.

We'll find the right candidates for you.
We'll help you find the tech talent you need to protect your organization, so you can focus on running your business.